The ever-growing digital world is constantly creating new risks of exploitation, abuse, and harassment of adults and children; however, this world also offers many new opportunities for organizations to improve their safeguarding efforts and practices. This webinar, part of a monthly series, discussed how digital technology can support the protection of vulnerable people, children, and staff. Bonnie Baker, Managing Director – myProteus; John Zoltner, Senior Advisor of Technology for Development and Innovation – Save the Children; and, Nora Lindström, Global Lead for Digital Development – Plan International, focused on tools and practical advice for securing and maintaining a robust safeguarding culture. These experts shared guidelines and good practice for leveraging digital platforms to create safe networks and engagement channels with their program partners. In the following paragraphs is a very brief summary of what each presenter discussed – including an overview of the Q&A portion of the webinar.
The first speaker was Bonnie who discussed components of Safeguarding & Lessons Learned for a successful safeguarding operating model. Whilst many NGOs realize they need to do something regarding Safeguarding, there isn’t a common understanding or alignment in the sector on what all the functions are, to ensure they are truly Safeguarding staff and beneficiaries. Proteus is known primarily as a change management company that tends to get involved in a number of different organizational changes. Bonnie has been engaged most recently in Safeguarding and Case management in the sector. Usually, the request for help by an NGO is made by asking IT to develop or buy a system to help address a problem.  However, there aren’t many systems that offer what the sector requires, and this goes back to the fact that fundamentally, the ways of programming, handling cases (internally or externally), are not clear. Internal to most NGOs, many do not understand what the full capability for safeguarding is. This means that IT departments are often at a loss to provide a system, when the core functions are not clear.
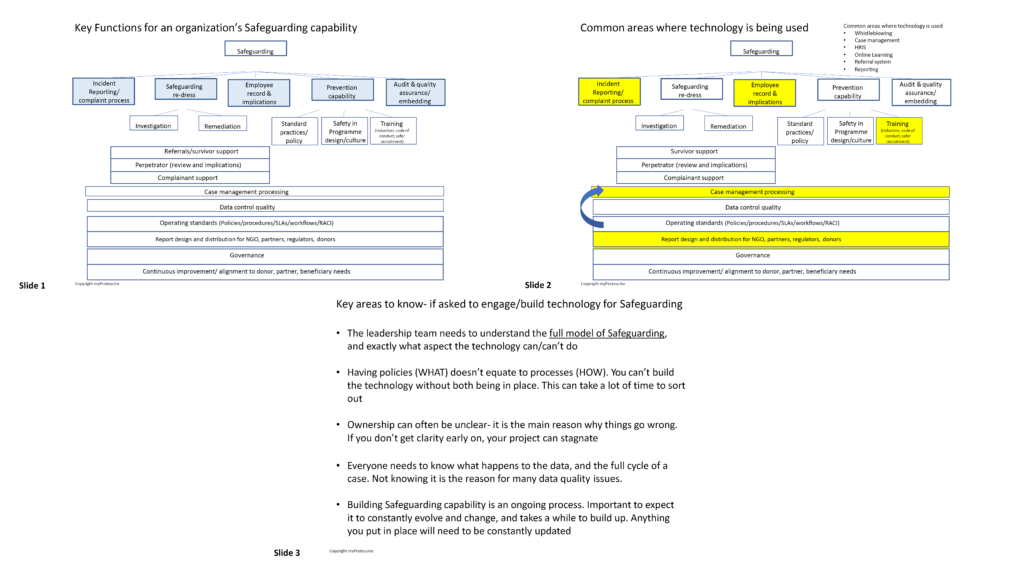
Bonnie used 3 slides to help guide her discussion (see below). In the first slide you can see how many things there are that NGOs need to have in order to have a proper safeguarding capability.
For all NGOs, the starting point needs to be in understanding ‘what’ Safeguarding it is. This was shared in slide 1. The discussion in slide 2 focused on where most NGOs think they need IT support. The problem arises when NGOs don’t realize that ALL functions in this operating model need to be understood in order to handle the full life cycle of what needs to be addressed. For example, it is one thing to be able to enable incident reporting. An incident of course should be processed as a case. However, if there are no clear processes in how to handle the survivor, perpetrator, or complainants, and importantly the ownership of who handles the cases, this becomes a challenge. When these are not clear, the value of any system is mute.
Also, before Bonnie moved onto her final slide, she wanted to ensure that the audience was aware that when implementing new safeguarding tools at an organization, each of the business units needed to agree to it and essentially get on board so that the organization’s policies can be easily translated into a suitable technological tool.  It is one thing to have ‘policies’, but the hard work is making them operational.
Finally, Bonnie graciously provides myProteus’ top 5 tips for someone who has been asked to build tech for safeguarding. Bonnie states the most important point is that you must ensure everyone in the organization can understand the full model of safeguarding, what all of the components of the model are, what elements can technology help you with; but, realistically the areas that technology cannot cover and a big part of that is the cultural change piece.  Bonnie shared that Proteus did build a maturity model that some NGOs are using, which explains ‘where do I start’, and ‘how to build a capability’. No NGO has it perfectly right, and it is important that they understand that this needs to evolve in a continuous way with programming. This only works if embedded into an NGO’s ways of working.
Following Bonnie’s excellent presentation, John is asked how Save the Children (STC) creates a culture of and good guidance for safeguarding children particularly when those programs might utilize tools as part of the programming. Initially, he takes a step back and says that the real issue that makes safeguarding such a necessity is the introduction of the digital tools and internet into programs. Technology can make development projects more effective but can also let bad guys more effectively access children. John offers some stats that should frighten everyone – in 2018 the National Center for Missing and Exploited Children received 18.4 million reports of potential online child sexual abuse and reviewed 45 million associated photos and videos. The number of these photos increased by over 1,000% from 2014-2017, and there are 750,000 men at any point in time trying to connect with children. This problem is particularly bad in the global south where most NGOs work. John claims that “in areas that haven’t been online as long as those in the developed world, there is less knowledge about what sounds right and what doesn’t; so, it is much more easier for kids who recently came online, in a culture where there’s not a lot of knowledge about these tools, to be tricked into or coerced into doing things that they regret in the futureâ€. This is something that I don’t think all of us may have thought of offhand!  Generally, John goes on to say, STC’s safeguarding policies are that all children have equal rights to protection from harm, everybody has a responsibility to support the protection of children, and organizations like Save the Children have a duty of care to children who we work with or come into contact with in any way.  Not to mention, they have a responsibility to ensure that volunteers, partners, and staff or anyone working in a Save the Children project receives a background check, which includes anyone who may even just come into contact with a child through virtual volunteering. The next step is ensuring that each and every one of these people is properly trained – which is mandatory – before they start work. Then, there is also annual training for all to complete. The whole essence of the principle is to minimize the risk to children while at the same time putting very strong mechanisms in place so that everybody knows what to do if they see something in the field or hear of something anywhere we think a child might be at harm who is in Save the Children’s care. With projects that use online technology, there obviously must be some special considerations first.
Last but certainly not least was Nora Lindström of Plan International who was asked to discuss leveraging digital platforms like Facebook as a means to build safe networks and interact with youth. She explains that at Plan they are increasingly using and interested in using online platforms like social media and networking sites to both connect with young people and children, as well as enable connections among children and youth. These types of platforms are great because they’re fast, convenient, and relatively low-cost to scale. Furthermore, Nora goes on to explain that they allow Plan to quickly reach and interact with quite large groups of children and young people in multiple formats in places where they might not be physically present. For example, videos, images, quizzes. The use of social media and networking sites allows Plan International to amplify young people’s voices, gain new insights and knowledge of issues that are important to them; which, is ultimately why it makes sense to them to utilize these tools regardless of the obvious digital divide that may exist in some places.  Like John, Nora understands the constant need to balance the risk vs. reward of utilizing these platforms when engaging with children. This is why Plan is primarily looking at how they can use social media and networking sites as a means of private engagement such as through private Facebook groups.  However, Nora states “when it comes to digital safeguarding, it is unrealistic to believe that Plan can safeguard against all types of safety and protection risks when the children use the internet, so instead we focus on building children’s online resilience and educating them on internet safety.†Not to mention, Plan can really only manage the online spaces that they have set up – like the Facebook groups that Nora discusses. One particular example of this that I found to be highly illuminating was when she explains that Plan can’t be responsible for content that children might encounter in the process of getting to that private Facebook group, in the same way the organization can’t be held accountable for something a young person might see out the window of a bus on their way to a workshop organized by Plan  – there is a limit to the duty of care. You’ll have to listen to the webinar to get the full discussion on Plan’s use of Facebook, but the bottom line is that it has been really successful so far and has helped them get new insights on what really affects girls once they build trust with the Plan moderators. The more comfortable they get the more willing they are to engage in discussions even on sensitive topics, which provides invaluable information for organizations like Plan when it comes to designing programming around this particular group – young women and girls.
After the wonderfully insightful discussions of the three presenters, we saved time for the audience to pose their own questions. The first question was asked to Nora about whether or not platform designers should take any responsibility when online abuse of children may occur.  She feels that certainly platform designers need to take responsibility here; a key reason that there is so much gender-based violence online is because there’s been such a lack of diversity among the creators of these platforms. The platforms have not been created with all these use cases in mind.  So, the platform owners and designers – those profiting from many of these platforms – need to think more about the users and keeping users safe. For example, Facebook – yes there is a function for reporting harassment; however, last time Nora checked (6+ months ago) it didn’t actually allow reporting of gender-based violence. We know that a significant number of girls and women are experiencing some type of violence on social media sites, but since you can only report general harassment and abuse you aren’t able to get a full understanding of just how much this is occurring. This is a design flaw in the platform, ultimately making some of the responsibility fall on the designers/owners. John adds that he agrees with using Facebook in Save the Children’s projects when safeguarding can be ensured, but the problem they face is that in many of the countries they work in – children are almost only accessing Facebook via mobile. They are not really accessing the internet in many other ways besides doing searches. Facebook is most of their experience of the internet. If one were to block it off and not allow them to use it in their programs then there is no way of anyone teaching them about how it works, what to do / what not to do. John continues on to say, “we know they are going to use it, that they are using it, so – we have to give them a model for how it can be used responsibly and safelyâ€.
In closing, several of the next questions dealt with data protection and are addressed to the presenters mostly together; however, the last question of the webinar is addressed to Bonnie. The question is about what sorts of steps and protocols does she see critical to ensure that staff don’t interact with youth outside the confines of their specific roles. Bonnie claims that “one thing is really important for organizations to put in place is an agreement that safeguarding as an issue is a cultural change programâ€. So, where she sees organizations having some challenges with it is when the full responsibility is sitting with HR to try and take ownership or just within programs; but, the best that she’s seen is in terms of how to embed this is having many different avenues to try and get the message across. The training that she has seen set has been on induction – she is seeing more NGOs understanding the need to embed training into the programs.  So, case management systems where they are being used effectively takes the mystery out of the equation for staff to understand what they need to do, where they need to go because the processes are embedded into the system. This way they will naturally go the course of what has been defined and agreed upon. This reduces the inconsistency from location to location if you have a global system that you put in place. But the constant communication from the organization in as many different places as possible to reiterate these messages and explaining what they need to do should be considered best practice.
By: Paul S Wiedmaier, ICT4D Knowledge Management, CRS